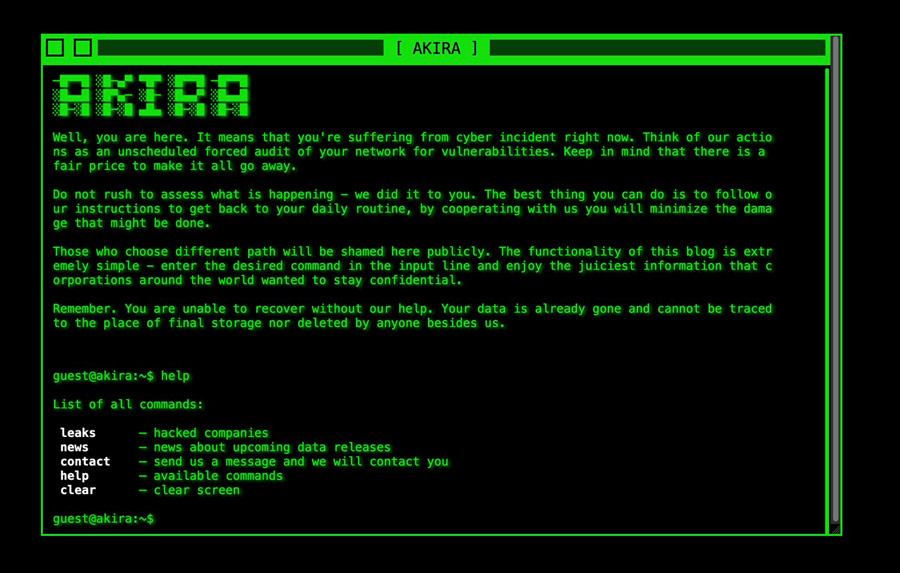
In 2025, the ransomware landscape has reached new levels of sophistication and danger. Threat groups like Lockbit, Ransomhub, Black Basta, 8Base, and notably Akira, are dominating the charts as the most active and devastating cyberattacks in the world. Among them, Akira Ransomware has proven to be one of the most persistent and dangerous, especially due to its targeted nature, stealth tactics, and double extortion model.
At Tictac Cyber Security, we’ve helped organizations across Greece and Europe recover from devastating Akira incidents, restoring operations with minimal disruption and providing a path to resilience.
Who is Akira Ransomware?
Akira emerged in early 2023 and quickly evolved into a high-profile Ransomware-as-a-Service (RaaS) operation. The threat actors behind Akira work with affiliates who infiltrate and compromise businesses before launching the encryption phase.
According to threat intelligence and law enforcement reports, Akira has already extorted over $40 million in ransoms. It is not a scattergun-type malware; it specifically targets high-revenue organizations. In Greece alone, at least four major enterprises have fallen victim to Akira since 2024, all of them with:
- Over 30 employees, and
- Annual revenues exceeding €10,000,000.
This is not coincidental. Akira is selective, strategic, and often lurks inside a company’s network for weeks or even months before executing its attack.
How Akira Attacks
Through incident response cases we’ve handled at Tictac, and detailed forensics investigations, we’ve identified a pattern in Akira’s modus operandi:
- It gains initial access often through compromised VPNs, phishing emails, or stolen credentials.
- The malware then performs reconnaissance, mapping the entire environment, escalating privileges, and preparing for lateral movement.
- Once established, Akira targets the client’s backups, attempts to delete or corrupt them, and then launches its encryption process.
- The primary targets are VMware ESXi hosts and all running VMs, crippling core IT infrastructure in one strike.
- Traditional antivirus or basic endpoint protection tools usually fail to detect or stop the attack due to Akira’s stealth and obfuscation techniques.
Double Extortion: The Second Punch
Akira uses a double extortion model. This means that even if your team attempts to recover from backups (assuming any survived), the attackers will threaten to publish your stolen data unless the ransom is paid. This puts businesses in a no-win situation: face operational paralysis or suffer public embarrassment, lawsuits, and regulatory penalties.
Free Decryption: A Glimmer of Hope?
In May 2025, a team from Fitsec publicly announced on Reddit that they successfully developed a decryptor for a variant of Akira that had been used between September 2023 and May 2025. According to their post:
“Despite the myth of Akira’s military-grade encryption, it was riddled with basic key generation flaws. With the right tools and GPU-acceleration, decryption became feasible.”
However, not all Akira infections are decryptable with free tools. Some victims may be infected with updated variants that do not share the same vulnerabilities.
That’s why a full forensic analysis is essential, and this is exactly where Tictac’s experience becomes invaluable.
Why Negotiating With Akira Can Be Dangerous
Some victims, in desperation, attempt to negotiate directly with Akira’s operators. This approach is riddled with risks:
- The attackers may take the money and disappear without providing a decryptor.
- They often demand additional payments once you’ve started engaging.
- You may unknowingly violate international sanctions by sending funds to a blacklisted entity.
Tictac offers safe, professional negotiation support (if necessary), always in compliance with legal frameworks and with your business interests at heart.
You Can’t Rely on Antivirus Alone
Akira has proven time and again that conventional antivirus solutions are insufficient. It evades detection through encrypted payloads, PowerShell-based execution, and advanced persistence techniques.
What your business needs is a robust Disaster Recovery Plan (DRP) and Immutable Storage solutions. These can drastically increase your odds of recovery without paying a ransom.
How Tictac Cyber Security Helps You Recover
Tictac Cyber Security specializes in ransomware incident response and has extensive experience dealing with Akira and similar advanced threats. Our service offering includes:
- 24/7 Incident Response Team with rapid deployment
- Forensics & root cause analysis
- Decryption assessment using both commercial and open-source tools
- Disaster Recovery support including virtual rehosting or physical restoration
- Legal & compliance guidance
- Secure communication and (if needed) negotiations
- Post-incident hardening: EDR, Zero Trust Architecture, and Immutable Backup design
Our goal is not just to get you back online—but to ensure this never happens again.
Conclusion
Akira is not just another ransomware strain. It is targeted, silent, and devastating. The average dwell time before encryption is weeks, and by the time the attack occurs, most victims are left helpless, with their backups wiped and their infrastructure encrypted.
Don’t leave your business exposed.
Whether you’ve been hit by Akira or want to strengthen your defenses before disaster strikes, Tictac Cyber Security is your trusted partner in resilience and recovery.