Protection from Infostealers, Password Leaks, and Computer Tracking
Are you wondering if your computer is being monitored?
Have you heard of malicious programs like infostealers (Lumma, Redline, etc.) that steal passwords, wallets, and personal data?
Our new Digital Risk Monitoring Service offers you complete control, analysis, and continuous monitoring to determine whether you are being monitored, whether your passwords have been leaked, and what data is at risk.

What are Infostealers, and why should they concern you?
Infostealers are malicious software that install on your computer without your knowledge, with the aim of stealing:
- Passwords (Chrome, Edge, Firefox, Opera)
- Cookie sessions (logins remain active even if you change your password)
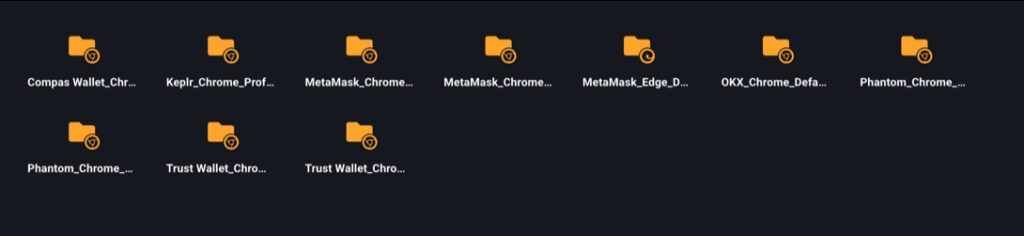
- Seed phrases from crypto wallets (MetaMask, Trust Wallet, OKX, Phantom, Keplr)
- Login credentials for emails, social media, VPN, cloud services
- Files, screenshots, and other sensitive information from your computer.
What Files Can an InfoStealer Collect?
An infostealer can gather everything someone needs to take control of your accounts, even your money or files.
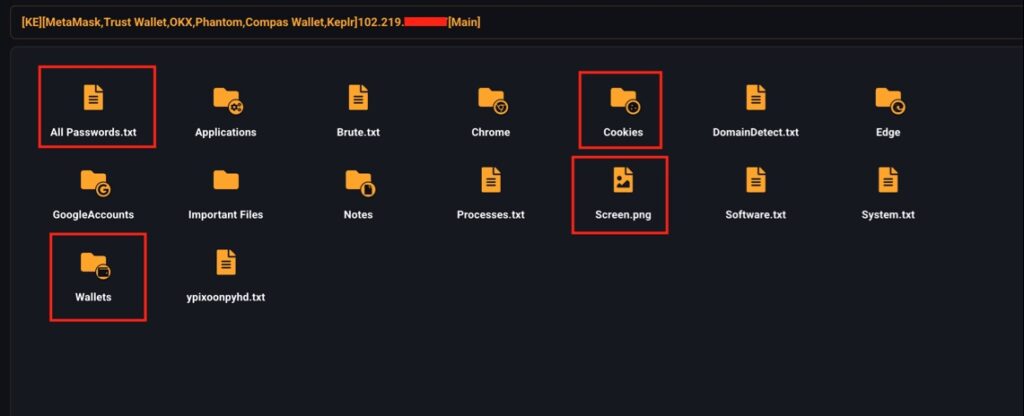
Specifically, it can collect files such as:
- All Passwords.txt: All passwords found in the system (browsers, applications).
- Cookies: These are active sessions for automatic login without a password.
- Wallets: Seed phrases and keys from crypto wallets (MetaMask, Trust Wallet, OKX, Phantom, etc.).
- Google Accounts: Google account access details.
- Screen.png: Screenshot of your screen at the time of infection.
- Important Files: It identifies as important (e.g., documents, PDFs, etc.).
- IP Address & Computer Name: Who was infected and when.
- Accounts and credentials for emails, corporate domains, and applications (Coinbase, Binance, Kraken, cPanel, social media).
- User credentials: All usernames and passwords found, along with the domains they belong to.
- Applications and services that have been exposed.
- Infection statistics: How many times it was detected, dates, operating systems.
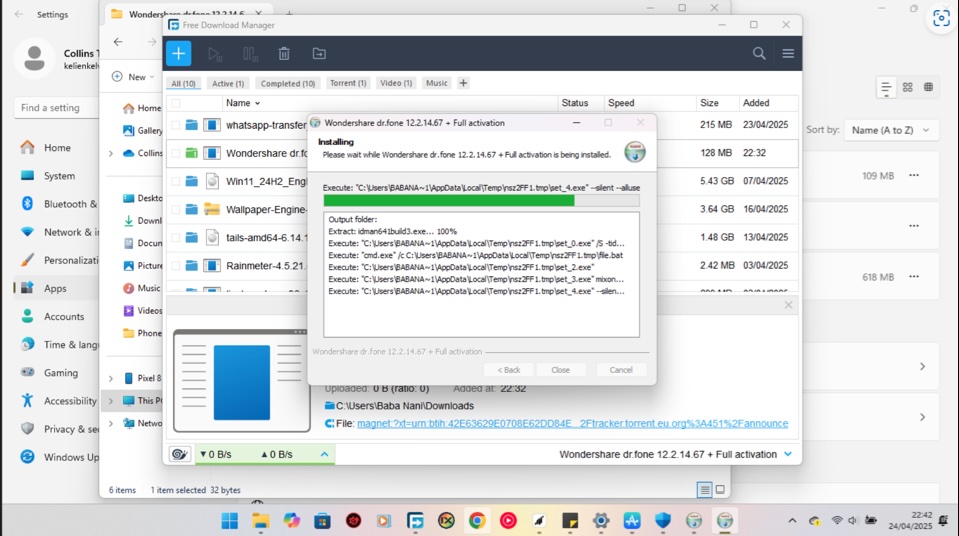
How Does an Infostealer Stay on Your System?
Once installed, an Infostealer remains active in the background, constantly collecting data while you use your computer unsuspectingly.
- It is installed to start automatically every time the computer is turned on.
- It continues to steal new data daily.
- It sends the data to attackers’ servers, which are used for attacks, money theft, blackmail, or further violations.
What Are You Risking Losing?
Someone gaining access to your files is the beginning, perhaps the least worrying.
The real problem begins when this data is leaked to dark web forums and sold to hackers.
What does this mean in practice? You could lose:
- All your saved passwords (Chrome, Edge, Firefox, Opera)
- Access to crypto wallets and your money
- Files, screenshots, and personal documents
- Professional and personal accounts
- Information that can be used for phishing, blackmail, or financial fraud
What does the Digital Risk Monitoring Service include?
1. Check for Infostealer Infection
- We analyze whether your computer is infected with Lumma, Redline, or another infostealer.
- We check if your credentials exist in logs circulating on the dark web.
2. Password & Email Leak Control
- We want to see if your emails and passwords have been leaked in known data breaches and infostealer logs.
- You are immediately informed of any leak with a detailed report.
3. Detailed Results Report
You will receive a detailed report that includes:
- List of exposed credentials (usernames & passwords)
- Cookie sessions that allow login without requiring a password
- Hacked Chrome, Edge, and Firefox passwords
- Seed phrases from crypto wallets (MetaMask, Trust Wallet, OKX, etc.)
- Leaked VPN, social media and email accounts
- Files and screenshots of your computer that have been intercepted
- Which applications, domains, and services have been exposed (e.g., Coinbase, cPanel, Google, Facebook).
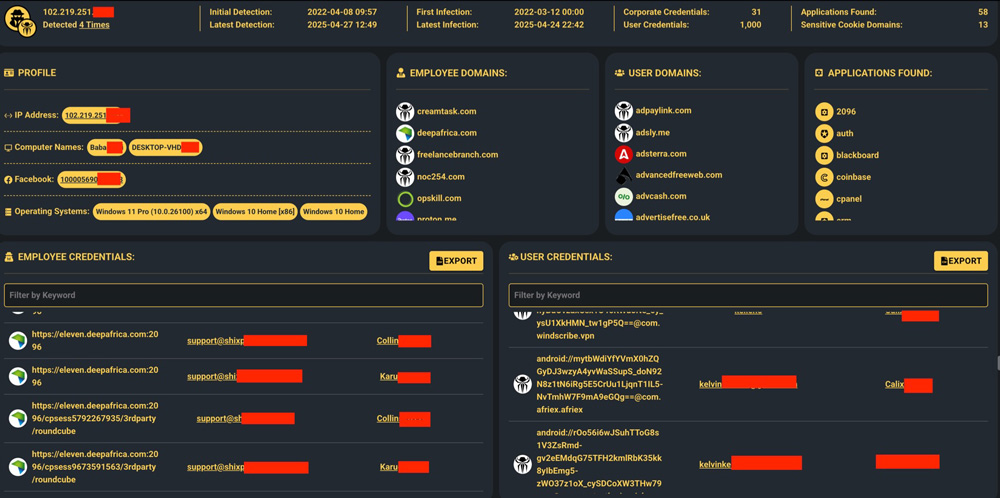
Reference Example:
In your report, you will see in detail all the files and data that were exposed on the infected computer: credentials, wallets, screenshots, cookies, and applications.
The following example shows how the infection profile is captured, with specific files, applications, domains, and accounts compromised by infostealer.
4. Continuous Monitoring (MSSP Model)
Within the Digital Risk Monitoring service, we also provide continuous monitoring of your digital security, not with a simple periodic check but based on the MSSP (Managed Security Service Provider) model.
This is a professional security model through which our team monitors in real time whether your information is leaked by an info stealer, whether new credentials appear in dark weblogs, or whether new threats arise that concern you.
In other words, you don’t wait for the check to be done again—we constantly remain on guard for you.
What does this monitoring include?
- Real-time monitoring: We monitor if your data appears again in leaks and notify you immediately.
- Repeated checks: We check again and again for new data that may have been leaked to prevent new threats.
- Specialized support: You receive guidance from our team on how to react, which passwords to change immediately, and how to reduce the risk of further breaches.
Indicative Service Prices
| Service | Price (One-time) | Price (Monthly) | Price (Annual) |
|---|---|---|---|
| Basic Control 1 Email/Computer | 150€ | 50€ | 500€ |
| Premium Control (3 emails/devices) | 350€ | 120€ | €1,200 |
| VIP Monitoring (continuous monitoring) | 400€ | 200€ | €2,000 |
The above prices are indicative and are adjusted depending on the number of emails, devices, and the depth of analysis required for your case. Prices do not include VAT.
Contact us if you need a more specialized check or have increased protection requirements.
Why Choose TicTac’s Digital Risk Monitoring Service?
At TicTac, we take digital security seriously. We don’t limit ourselves to a simple audit. Still, we offer you a complete monitoring, analysis, and guidance service so you always know if you are exposed and what to do immediately.
- We use enterprise-grade tools that are not available to the general public.
- We detect and analyze logs from Lumma, Redline, and dozens of other infostealers.
- We provide personal counseling and guidance.
- You are immediately informed if your computer is being monitored or your passwords have been leaked.
Frequently Asked Questions (FAQ)
1. How will I know if I am being monitored?
With our audit, you will receive a detailed report with all exposed credentials, files, and data that have been intercepted by the infostealer, as well as from where and when.
2. What is Infostealer?
It is malicious software that steals passwords, cookies, wallets, files, and screenshots from your computer without your knowledge.
3. Have my passwords been leaked?
We will inform you exactly which passwords, emails, and accounts have been leaked, which breaches have occurred, and whether your crypto wallets are at risk.
4. How secure is the service?
The analysis is conducted with absolute confidentiality, and the highest standards protect your data.
Strengthen Your Security with 3 Simple Steps
Find out if your computer is being monitored or if your passwords have been leaked!
Contact Us
Talk to an expert about your needs
Get a Quote
One of our experienced engineers will assess your needs and provide you with a customized solution to protect your business best.
Strengthen Your Security
Reduce risk and boost your business efficiency with the most modern cybersecurity tools
Representatives of the largest Cyber Security Companies
Guaranteed protection solutions from the most reliable companies in the field.
















